How To Use an Information Flow Map to Determine the Scope of Your ISMS

By: Brett Davis, senior CISO consultant
An information security management system (ISMS) is a critical component of every organization. An ISMS consists of the documented set of security controls in place to protect the confidentiality, integrity, and availability (the CIA triad) of data.
It’s important for an ISMS to have clearly defined scope and boundaries. The scope determines which information is protected by security controls, and which information falls outside of your ISMS. This typically includes the entirety of an organization’s systems, processes, locations, products, and third parties that need security controls in place. The scope communicates the business operations that are covered by the ISMS to all key internal and external stakeholders. It’s especially important for your organization’s auditors, who will rely on the scope to determine whether the systems within your ISMS are appropriately protected.
There are a number of ways to determine the scope of your organization’s ISMS. Creating an information flow map is an important process that can help you identify these boundaries.
What is an information flow map?
An information flow map is a diagram that maps the way that information flows through an organization. It identifies the movement of data within an entity and data that is communicated and received externally.
To get started on an information flow map, begin by listing the objects within your system and discussing internally the major inputs and outputs of your system or business model. Objects include any tool, website, application, software, or database that data flows through. For example, if your organization uses Salesforce for customer relationship management, Salesforce should be listed as an object. Each object should have an input and output. Major inputs and outputs are the type of information that flows between objects within the system. This is important because the type of information can have a big impact on scope—for example, if personally identifiable information (PII) flows between objects, that data needs to be protected with different security controls than if general text flowed between the objects. Once you understand the objects, inputs, and outputs within your organization, create a diagram that depicts the way data flows within your business.
Once the diagram is created, it can be helpful to add specific details and use a key to help those viewing the diagram understand it. For example, companies may choose to color code the objects that store PII, or use different shapes to designate internal versus external objects. Overall, the diagram should be shared internally and high-level enough that it could be easily understood by anyone in the organization. If more technical detail is needed to describe how data moves between certain objects, add another layer to the diagram to explain any complex workings as needed. See an example below.
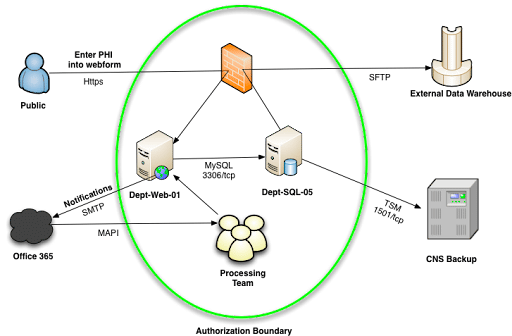
Source: University of Florida Information Security Program
There are a number of tools available that can help organizations configure these diagrams to be accurate and aesthetically pleasing, and many of them are free to use. LucidChart, Vizio, and Miro are just a few examples of helpful tools. The PCI Security Standards Council also has a useful toolkit for defining the boundaries of your ISMS.
An information flow map should be updated anytime a process or information flow changes. At a minimum, it should be reviewed annually.
The benefits of an information flow map
An information flow map illustrates the way information flows and which objects are most important to the information system. Once in place, this can help an organization identify risks from potential weak points, redundancies, or single points of failure. For example, if a lot of information flows through a single object, and that object fails, it could cause the entire system to fail.
With a visualization of potential risks associated with the information system, an organization can then determine the security controls that need to be implemented to mitigate those risks and protect the system overall now that a scope is clearly defined.
With a solid information flow map in place to determine the scope of an ISMS, an organization is better prepared to handle overall security risk.
Interested in learning more, or need help creating an information flow map for your organization? Contact us today.
About the Author

Brett Davis, senior CISO consultant
As a Senior Consultant in BARR Advisory’s CISO Advisory practice, Brett Davis evaluates the design and effectiveness of clients’ technology controls to prevent breaches and incidents and identify opportunities to operate more efficiently. Brett is recognized as a diligent, disciplined individual that goes above and beyond for his team and his clients.
Prior to BARR, Brett served in the United States Navy for six years, where he was a member of the elite Navy Special Warfare community that conducted special operations. After his service, Brett went on to mentor veteran students—providing support and positive influence to help them achieve academic, career, and life goals.
Brett holds a Bachelor of Science in Accounting from the Bloch School of Management at the University of Missouri-Kansas City.